Penetration Testing Services
Let us find exploitable technical vulnerabilities before someone else does.
PCS delivers Penetration Tests, across complex organizations, to meet their needs
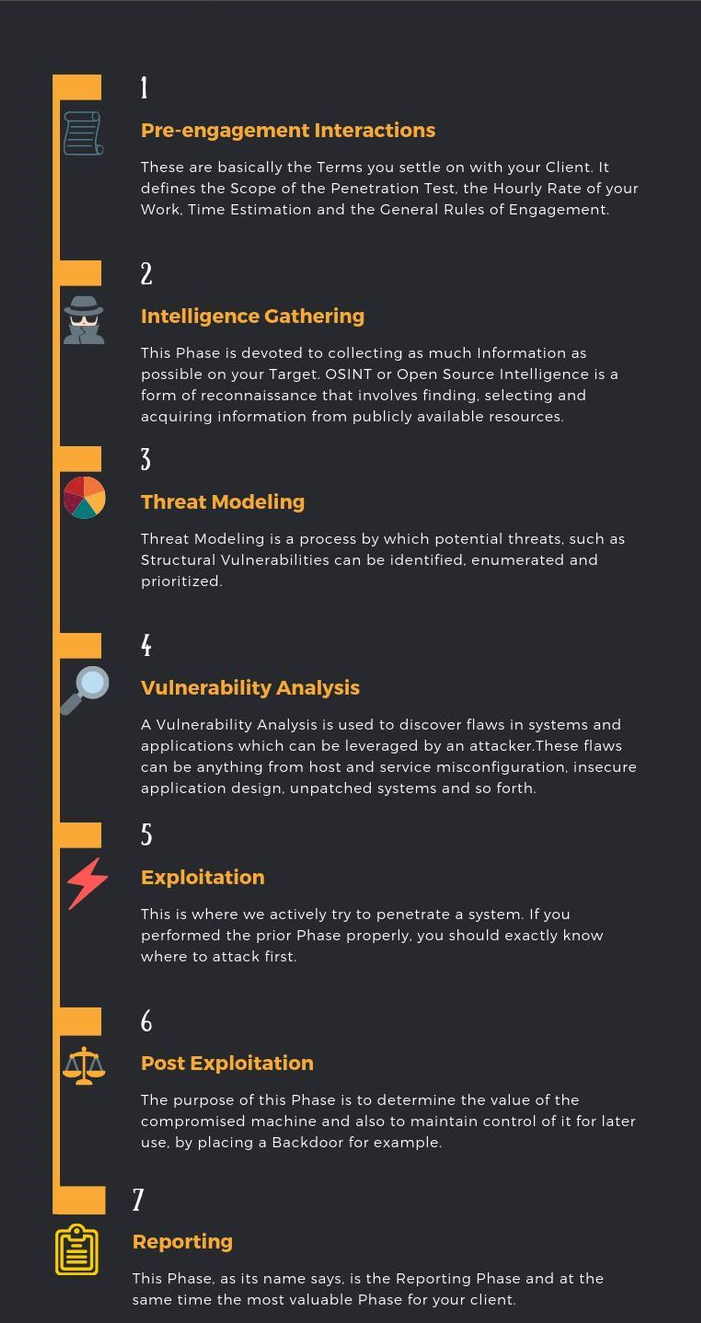
The Seven Phases of a Penetration Test
Pre-Engagement Interactions
During this pre-phase, PCS will outline the logistics of the test, expectations, legal implications, objectives and goals the customer would like to achieve.
Intelligence Gathering or Open Source Intelligence (OSINT)
On this first step PCS works on gathering as much intelligence on your organization and the potential targets for exploit.
Threat Modeling
During the threat modeling PCS identifies targets and maps the attack vectors. Any information gathered during the Reconnaissance phase is used to inform the method of attack during the penetration test.
Vulnerability Analysis
A Vulnerability Analysis is used to discover flaws in systems and applications which can be leveraged by an attacker. These flaws can be anything from host and service misconfiguration, insecure application design, un-patched systems and so forth.
Exploitation
With a map of all possible vulnerabilities and entry points, PCS begins to test the exploits found within your network, applications, and data. The goal is to see exactly how far we can get into your environment, identify high-value targets, and avoid any detection.
Post-Exploitation, Risk Analysis & Recommendations
After the exploitation phase is complete, the goal is to document the methods used to gain access to your organization’s valuable information. In this phase PCS determines the value of the compromised systems and any value associated with the sensitive data captured.
Reporting
Reporting is often regarded as the most critical aspect of a pentest. It’s where you will obtain written recommendations from PCS and have an opportunity to review the findings from the report

Benefits of Penetration Testing
Avoid revenue loss and reputational damage
In the case of a data breach, your company’s reputation will suffer, which usually leads to a loss of customer confidence and causes a drop in revenue. Establish a comprehensive security program, which will protect your infrastructure and application ecosystem.
Proactively identify vulnerabilities
Employing penetration testing services helps identify the major exploitable vulnerabilities. It helps to reveal the risk, your company is exposed to, and its impacts.
Expose the real-world attack vectors
By modelling a real attack against the target system, it is possible to have an unbiased look at the company’s protection level and check whether its security mechanisms are effective in practice.
Validate existing controls and develop guidelines for remediation
Any identified vulnerabilities will be given remediation techniques applied immediately to ensure your IT and network infrastructure is properly protected.
Meet regulatory requirements and avoid fines
Businesses operating in highly regulated industries (e.g., healthcare, financial services, etc.) require security investments and help from security researchers who can provide penetration testing services. The security guidance is designed to make their businesses comply with existing regulations.
Avoid business disruptions
No business is immune from cyber-attack, so scheduling regular penetration tests and network security audits is a way to help prevent interruptions to normal business operations.



